Continuous Penetration Testing
Remove the artificial time constraints on security tests. We combine continuous attack surface management with expert human testing to detect changes and assess risk in real-time.

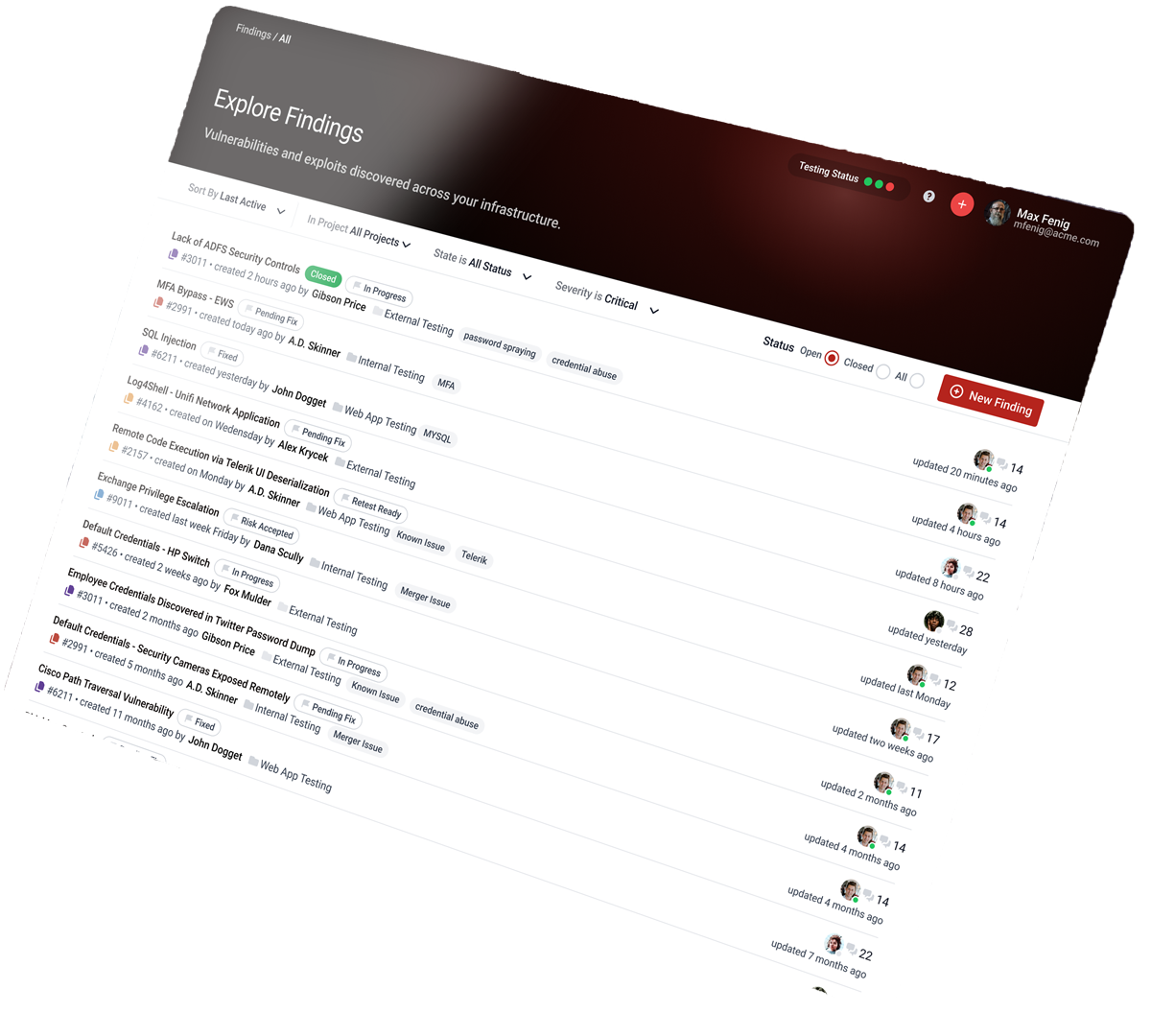
Why Point-in-Time Testing Fails
Pentesting is painful. It’s hard to schedule, communication is slow, and the results are outdated fast. Staying secure, and compliant, should not depend on once-a-year testing.
"Doing pentests is hard."
Traditional penetration tests are harder than they should be. Scheduling takes weeks, results are outdated by the time they are delivered, and they miss constant changes in your environment.
"Communication is slow and fragmented."
Communication with your vendor can be slow, leaving your team waiting for weeks with little visibility into progress or findings. Then when moving into remediation, there can be delays as testers move on leaving you exposed.
"Falling out of compliance between tests.”
It’s tough to meet framework standards when your penetration tests only happen once or twice a year. Point-in-time reports quickly become outdated, leaving gaps auditors notice and attackers can exploit.
Benefits of the Sprocket Approach
At Sprocket Security, our CPT approach is built to go beyond the limitations of point-in-time testing. By adapting to your evolving attack surface, we deliver real-time insights, faster remediation, and stronger security outcomes. Here’s how our approach delivers tangible value to your business:
__________________________________________
Discover & Remediate
Act on the findings that matter most in real-time.
Traditional testing leaves you in the dark between reports. With Continuous Penetration Testing, our expert team of testers and detection automation provides you full visibility into real threats as they appear. This removes the time constraint of having to wait for your next scheduled test.
- Assign users to findings to accelerate time-to-remediation
- Collaborate in real-time with testers
- Manage states and statuses of findings


Know Your Enemy
Attack Narratives turn the black box into clear, actionable insight.
With Continuous Penetration Testing, you don’t get a snapshot. You have unlimited retesting to verify fixes, validate controls, and close the loop on remediations. Our testers describe the paths and procedures to help you understand how exploits happen through attack narratives to better strengthen your security posture during patching and IT infrastructure maintenance.
- Unlimited retesting to confirm vulnerabilities are truly fixed
- Step-by-step narratives that map attacker behavior
- Continuous validation aligned with real-world threats
Report Successfully
Track real-time progress and generate on-demand reports.
The Sprocket Portal delivers real-time analytics on your remediation velocity, attack surface, threat detection, and important findings through on-demand reports.
- Provided attestation reports for third parties
- Download PCI, SOC2, and other compliance ready reports
- Generate Executive Summaries for leadership and stakeholders


Human-driven Testing
Experience seamless and organized penetration testing services.
Sprocket's Service Delivery team delivers continuous penetration testing across external and internal networks, web and mobile application testing, purple or red teaming, and social engineering all maintained within the Portal.
- Manage scoped assets by individual projects
- Add services and assets as needed
- Browse and filter findings by project scope
Continuous Testing
Expert-led, automated, and always with a human in the loop
As your attack surface evolves, our testers remain alert by applying real-world techniques to continuously attempt to penetrate your network through new exposures, misconfigurations, and vulnerabilities the moment they appear.
External Penetration Test
Discover risks and security vulnerabilities utilized by real-world attackers. Find forgotten and vulnerable applications as well as the more uncommon attack paths.
Internal Penetration Test
Protect your organization's most critical assets from insider threats. Testers will move laterally and escalate privileges to gain access to your organization's infrastructure.
Social Engineering
Employees can pose the greatest risk to your most important assets. Test your security posture and controls through a series of different social engineering campaigns.
Web Application Testing
Bleeding-edge attacks can promptly be tested across all of your applications. Our testing teams work to identify risks affecting your applications before potential breaches occur.
Continuous Human & Automated Security
The Expert-Driven Offensive
Security Platform
Continuously monitor your attack surface with advanced change detection. Upon change, testers and systems perform security testing. You are alerted and assisted in remediation efforts all contained in a single security application, the Sprocket Platform.
Expert-Driven Offensive Security Platform
- Attack Surface Management
- Continuous Penetration Testing
- Adversary Simulations
