Quick queries for Solarwinds Orion
URL endpoint:
/Orion/Login.aspxShodan queries:
- http.title: "SolarWinds Orion"
- http.favicon.hash: -1776962843
- http.title: "SolarWinds Orion" http.favicon.hash:-1776962843
Google Dorks:
inurl:/Orion/Login.aspxRecent reports from FireEye revealed a large-scale campaign to infect company networks using a modified version of the SolarWinds Orion monitoring agent.
To give you a clear understanding how continuous penetration testing can help you enumerate the possible use of SolarWinds Orion we’re going to highlight methodologies we use every day at Sprocket. While this isn’t a vulnerability by itself, insight into our process will:
- Showcase the scale at which Sprocket can collect information
- Highlight tooling we use every day
- Demonstrate the significant impact of this supply-chain attack
What is SolarWinds Orion?
SolarWinds states that the product allows users to:
- Help organizations meet service-level agreements
- Scale to meet IT needs
- Provide seamlessly integrated monitoring capabilities
We won’t go into detail, but the recent FireEye report details a compromise of SolarWinds and a subsequent backdoor into their monitoring agent.
How would you hunt for an internal product?
You may wonder: “How do you hunt for something that’s an internal product?” What we’ve found organizations often expose the Orion login endpoint to the internet. The process for detecting usage of the product is the same internally, however. Due to the size of some internal domains, admins may be unaware of the usage of Orion and will need to search for it.
With the knowledge of the Orion authentication endpoint and a large enough dataset, we can find organizations possibly affected by this attack campaign.
First, we did some research and tried to find endpoints indicating the use of Orion. After some digging, we found the following login portal page:

Further research revealed that these portals look different depending on the version in use:


Some even include organizational branding:
These endpoints all have two things in common:
- They’re accessed using the URL scheme “/Orion/Login.aspx”
- They use the page title value, “SolarWinds Orion”
With this information, we can use existing tooling and datasets to find live login portals.
Shodan
A great place to start is shodan.io. Shodan provides a search engine for identifying technologies and services available on the internet.
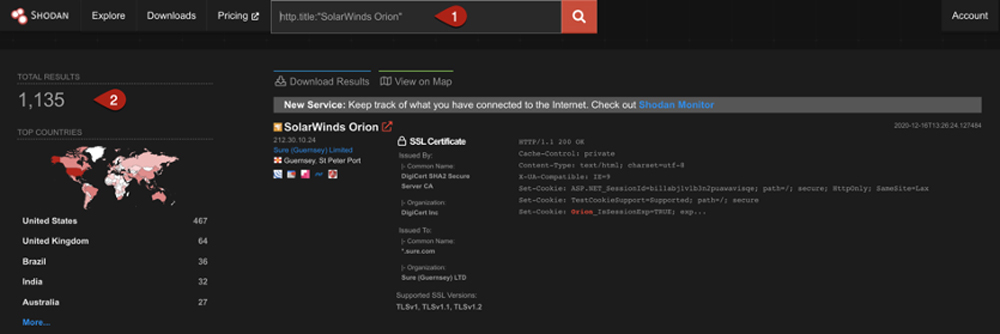
In a recent update, they added a filter value that allows users to search for strings in a webpage’s HTML contents. With the search below, we’ll quickly find a ton of exposed SolarWinds Orion login pages.
We started with this search query:
http.title:"SolarWinds Orion"
Shodan won’t find everything out there, but the service gives us a good jumping-off point. The results in the screenshot below were returned using the query above:
Some additional search queries we could use to get a bit more coverage:
http.favicon.hash:-1776962843
http.title:"SolarWinds Orion" http.favicon.hash:-1776962843Programmatic Detection
At Sprocket, we would use a list of target organization URL’s to scan for endpoint exposure. We first get a list of target domains and IP addresses. With that information, we use a simple one-liner to extract valid endpoints using the tool httpx and nuclei.
cat orion-hosts.txt | httpx -silent | nuclei -t solarwinds-orion.yamlWith your list of desired hosts, run the command above, substituting in your list where we cat the file orion-hosts.txt. Your output will look something like the following:

After these initial manual checks, we often create custom modules for our monitoring engine to watch for these endpoints being exposed by clients.
Some other ideas
Hypothetically, if we want to do a larger scale search for these endpoints we could:
- Download a dataset, like the ones Rapid7 provides
- Extract valid web applications
- Subsequently check if the URL endpoint mentioned earlier is active. Here’s the link to the datasets available: https://opendata.rapid7.com
There’s potential for additional surveying using the Common crawl dataset and AWS Lambda in a way similar to what Andrés Riancho did in a paper about collecting AWS Cognito credentials.
Furthermore, recent research has revealed a list of internal domain names exposed by the decoding of command-and-control infrastructure DNS addresses. A link to the script used to decode already discovered domains is linked below.
https://github.com/malvidin/SunBurst_DGA_Decode
Enumerating a full list of these domains is difficult when using traditional open-source intelligence methods. However, members of the information security community have now published lists of internal domains associated with known command-and-control infrastructure. This list contains what appears to be the internal domains of Fortune 500 companies and government agencies.
https://pastebin.com/raw/G7mnW5Zk
Wrapping it up
Regardless of the possible use case, we hope this article provides a look at the collection and monitoring process we use at Sprocket to simulate the actions of real-world attackers. Attackers collect indicators of technologies in use and use that information to scan the internet looking for vulnerabilities to be exploited.
This supply chain attack is going to be a headache that organizations suffer through for at least a year. The impact and scope of intellectual property and monetary theft isn’t yet known.
SolarWinds claims that the backdoored client affected at least 18,000 customers. While we may feel this is a small number, we can’t forget attackers could easily leverage their backdoor to gain access to sister organizations and downstream companies.
SolarWinds reached out to clients to inform them of the breach, but many organizations lack the ability to respond to this event and don’t know how to secure their network going forward.
Questions? Want to learn more about how continuous penetration testing works? Send us a note any time.




