No one wants to be the next cybersecurity news headline. For enterprises and their web apps, they can keep it that way by leveraging guidance from OWASP’s Top 10 risks to help to streamline enterprise application defense strategy, ensure infrastructure remains free from commonly exploited web application vulnerabilities, and help focus remediation efforts concerning identified defects.
The digital business landscape is increasingly challenging due to heightened competition, reduced budgets, staffing challenges, and constraints from business stakeholders. This can lead some development teams to release insecure web applications with internet-exposed infrastructure and vulnerabilities, which can invite a cybersecurity breach. The non-profit Open Web Application Security Project (OWASP) offers technical awareness documentation known as the "OWASP Top 10," which outline prioritized areas of concern for web development teams as they build and release internet-facing applications. This article will preview the OWASP Top 10 risks, demonstrate how cybercriminals exploit web application vulnerabilities outlined in the OWASP Top 10 and provide remediation and defense considerations for enterprises to strengthen cybersecurity controls for web development and reduce their web application attack surface.
What are the OWASP Top 10 Risks?
The OWASP Top 10 risks gain their respective rankings from research or vulnerable code submissions offered by project members, security consulting organizations, bug bounty hunters, and other cybersecurity specialists3.
Analysis performed against vulnerable code samples determines how often a given vulnerability is detected, ranking each risk topic within the Top 10 hierarchy. The infographic below summarizes the OWASP Top 10 and prioritizes each area of risk to help the enterprise focus its remediation strategy around the most concerning cybersecurity gaps.
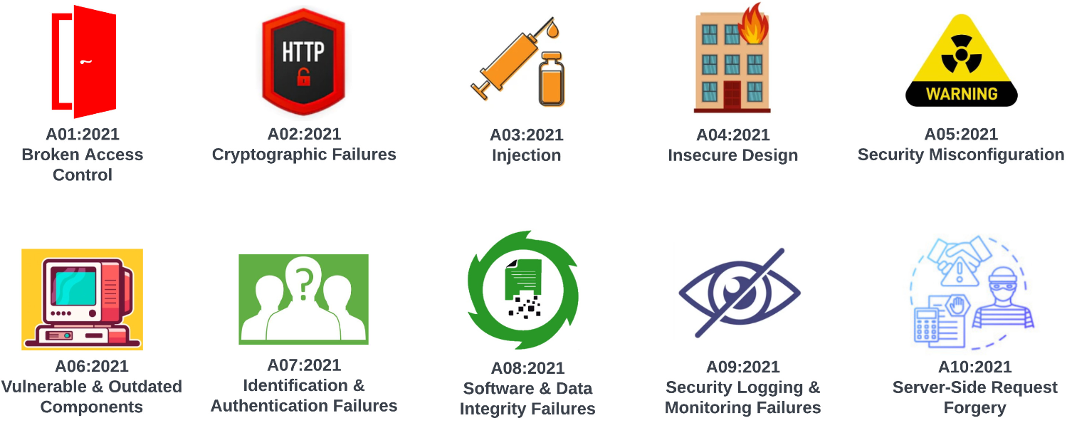 Figure 1 – The OWASP Top 10 controls, prioritized per the current ‘2021’ standard.
Figure 1 – The OWASP Top 10 controls, prioritized per the current ‘2021’ standard.The Top 10 standard is reviewed and updated every 3 years, holding to this schedule since 20043. As reviews of the Top 10 risks occur, some risks move position within the hierarchy (i.e., moving from position A05 to A01 for example) or new risks emerge within the next 3-year release.
OWASP also features a wide variety of tools; which will be showcased through this article, that assists developers and security professionals with understanding each risk in-depth and commensurate cybersecurity controls. This article will demonstrate the exploitation of several Top 10 risks using the Damn Vulnerable Web Application (DVWA), as it’s expressly configured to highlight sub-optimal cybersecurity practices relevant to modern web applications.
A01:2021 Broken Access Control
Broken access control occurs when an access principal, like a user account or API, may perform unauthorized actions which violate their assigned permissions and rights. Common vulnerabilities include non-secure object references, access control bypass, privilege escalation, forceful browsing, and metadata tampering. Below is an example of how an intercepting proxy like the OWASP Zed Attack Proxy (ZAP) may provide session ID forging opportunities to would-be hackers.
A form of broken access control, session ID forging allows a website to be accessed without knowledge of legitimate credentials by observing and accurately predicting how the site generates session IDs and assuming the identity of a valid session through impersonation.
 Figure 2 – Viewing the source code and generating multiple sessions shows each new session increments predictably and consecutively by 1 per the $SESSION variable logic (last session id’]++;)
Figure 2 – Viewing the source code and generating multiple sessions shows each new session increments predictably and consecutively by 1 per the $SESSION variable logic (last session id’]++;)The above risk could be effectively mitigated by ensuring sessions are generated with a Cryptographically Secure Pseudorandom Number Generator (CSPRNG), to prevent guessing attacks and further implementing session management features, enforcing lifetime limits on session cookies or tokens5.
The ‘Secure’ cookies attribute could also be set to ensure cookies generated between the client and server infrastructure leverage encryption, further disguising the true value of the Session ID cookie.
Let’s skip onto Injection, as it can really highlight how insecure web forms and data controls may easily provide cybercriminals the sensitive data they are looking for without having to perform extensive network infrastructure compromise.
A03:2021 - Injection
Injection risk stems from a lack of proper data sanitization, filtering, or logical constraints placed against web forms or other inputs provided by users to the application. Injection prevention efforts typically involve separating user-supplied information from database-level commands and SQL queries that allow web apps to function.
Examples of mitigating controls include a combination of server-side input validation, parameterized queries, and character escaping. Basic examples of a command and SQL injection vulnerability are highlighted below, where parameters associated with specific web application forms do not securely restrict the character types or length of data provided in a form field.
 Figure 3 – The ‘$target’ parameter associated with the ‘Ping a device’ source code (not shown) allows non-numeric system commands to be submitted to the backend database, revealing the ‘passwd’ directory contents.
Figure 3 – The ‘$target’ parameter associated with the ‘Ping a device’ source code (not shown) allows non-numeric system commands to be submitted to the backend database, revealing the ‘passwd’ directory contents.The next example will overview dumping password hashes from DVWA using a combination of OWASP ZAP and sqlmap. When intercepting HTTP GET requests using ZAP, the data can be copied into a request file which can be passed back into sqlmap for some basic automation tasks. sqlmap can then replay the request to dump the passwords stored in the backend database.
 Figure 4 – The User ID function will be used to capture HTTP request data which is later exploited
Figure 4 – The User ID function will be used to capture HTTP request data which is later exploitedAfter capturing necessary details from a proxied request in ZAP, a request file is created with the HTTP request details and then referenced within the below sqlmap command.
 Figure 5 – The ‘id’ parameter is confirmed as injectable by sqlmap and used as a vector to extract then crack 4 user account passwords which are revealed in plaintext.
Figure 5 – The ‘id’ parameter is confirmed as injectable by sqlmap and used as a vector to extract then crack 4 user account passwords which are revealed in plaintext.The last few examples highlighted only a small portion of the cybersecurity risks enterprises need to account for within OWASP’s guidance. According to Incident Response firm LIFARS, web application attacks are becoming more prevalent in high-profile cybersecurity breaches, accounting for nearly 50% of documented breaches8.
Even when fully mitigating the risks outlined in the OWASP Top 10, enterprises must still ensure they strive to satisfy other cybersecurity controls and frameworks such as NIST Cybersecurity Framework and the Center for Internet Security Top 18 controls which provide security configuration baselines for modern database management, systems and web server platforms. Despite best efforts surrounding remediation and defense efforts, Cybercriminals are evading network security controls through several obscure means, which are summarized below and can be reviewed further using this complimentary content[W1] :
- Obtaining access through exposed administrative interfaces or Zero Day vulnerabilities (e.g., WordPress CMS, etc.) and then pivoting into the internal network7
- Modifying the User-Agent header to evade detection throughout an attack or confuse logging and detection mechanisms8
- Leveraging an IP address rotation solution or proxy service to cover brute forcing efforts8
- Leveraging public cloud infrastructure such as Amazon API gateway to bypass rate limitation features of Web Application Firewalls (WAF)
When it comes to web application security and ensuring the attack surface is sufficiently minimized, this article provides some introductory resources that can help educate web developers on security best practices while also providing tools to reduce the likelihood of a cybersecurity incident. Enterprises must strive to keep pace with their adversaries and broaden their approach to web application cyber defense or face becoming another negative statistic.
Most web application defense strategies center on the placement of Web Application Firewall (WAF) solutions, like those offered by Cloudflare, in front of their infrastructure to repel sophisticated attacks. Developing comprehensive cybersecurity policies and subscribing to security advisory services for in-use products, which lead to the execution of patch management processes, are other key control to avoiding web application cyberattacks. A defense-in-depth approach will help ensure applications, infrastructure, and data remain secure while allowing the business to constantly provide its intended value back to its stakeholders.
References
- 1 Who/What is OWASP - https://owasp.org/
- 2 OWASP Relevance in 2022 - https://thehackernews.com/2022/10/does-owasp-top-10-still-matter.html
- 3 How OWASP Data is Gathered To Select the Top 10 Risks - https://owasp.org/www-project-...
- 4 OWASP Top 10 history - https://www.hahwul.com/cullinan/history-of-owasp-top-10/
- 5 OWASP Session Management Cheat Sheet -https://cheatsheetseries.owasp.org/cheatsheets/Session_Management_Cheat_Sheet.html
- 6 Web Attacks on the Rise - https://www.lifars.com/2022/01...
- 7 Exploiting WordPress vulnerabilities to pivot to internal networks – https://www.securityweek.com/w...
- 8 Changing User Agent Header for Spoofing - https://51degrees.com/blog/use...



