Overview
The key to our engagements often and unfortunately involve the discovery of credentials on internal network file shares. We’re going to show you how we find cleartext password storage problems and how to address them.
This issue is rampant and even has its own MITRE mapping:
Unsecured Credentials: Credentials In Files (MITRE T1552.001) Unsecured Credentials: Credentials In Files

Essentially, if an attacker gains credentialed access to your network, they can use open source and native Microsoft Windows tooling to search for files containing sensitive information. Not only can this lead to PII disclosure, but also privilege escalation and domain takeover.
Description
Attackers carry out the following steps to exploit this security best-practice violation:
-
Gain access to the organization’s internal network
-
Capture, guess or use social engineering to acquire cleartext credentials, most often for a low-privileged domain user
-
Leverage tools to search network shares for files named or containing words such as
- password
- credentials
- id_rsa – aws
-
These files, when found, often contain cleartext credentials for privileged service accounts used to escalate privileges and takeover a company’s domain
-
Real world attackers will then use these credentials to laterally move throughout the network as a legitimate user. They then do the following:
- Exfiltrate sensitive business information
- Disrupt company services
- Deploy ransomware
A cool tool for offensive operations
My favorite tool for carrying out this TTP is MANSPIDER. I know, I know, the name leaves a bit to be desired. Regardless, it’s a fantastic tool.
MANSPIDER not only searches for file names containing high-value wording but also has the ability to read the contents of:
-
Images
-
Microsoft Office documents
-
And … pretty much anything else you can imagine
See the command below for an example of this tool in action.
python3 manspider.py smb.masscan.txt -u Administrator -p 'B@dP@assw0rd!' -c password krd keepass kdbx credential azure O365 ADFS secret -t 50
The command will run, spider network shares and download/log all matching files. You can then navigate to the loot directory in the MANSPIDER local repository and review the collected files.
Example Case Study
Instead of using the tool above, let’s showcase us carrying out this attack the old-fashioned way.
Sprocket started a new engagement unlike any other. The targeted organization exposed a Microsoft Exchange server to give users access to their mailboxes and other company services. Using open-source tooling and custom wordlists, Sprocket enumerated valid usernames and attempted to guess credentials.
Sprocket was successful in guessing credentials for a forgetten service account with the username, “testmail.” However, this account couldn’t authenticate to the companies VPN due to a strong multi-factor authentication (MFA) programthe organization implemented.

Regardless of the lack of VPN access, this username and password combination was used to abuse the Microsoft Exchange ActiveSync protocol and the tool, Exchanger, to extract DNT dump (This is one of our favorite attacks, by the way.).
The DNT dump was performed using the Impacket tool, Exchanger. We then parsed out internal hostnames of workstations and servers.
exchanger.py ACME/testmail:Password1@mail.acme.com nspi dnt-lookup -lookup-type EXTENDED -output-file exchanger.output.txt
We then searched file shares for sensitive information in Word documents in the context of our compromised user. An example of this is shown in the screenshot below:
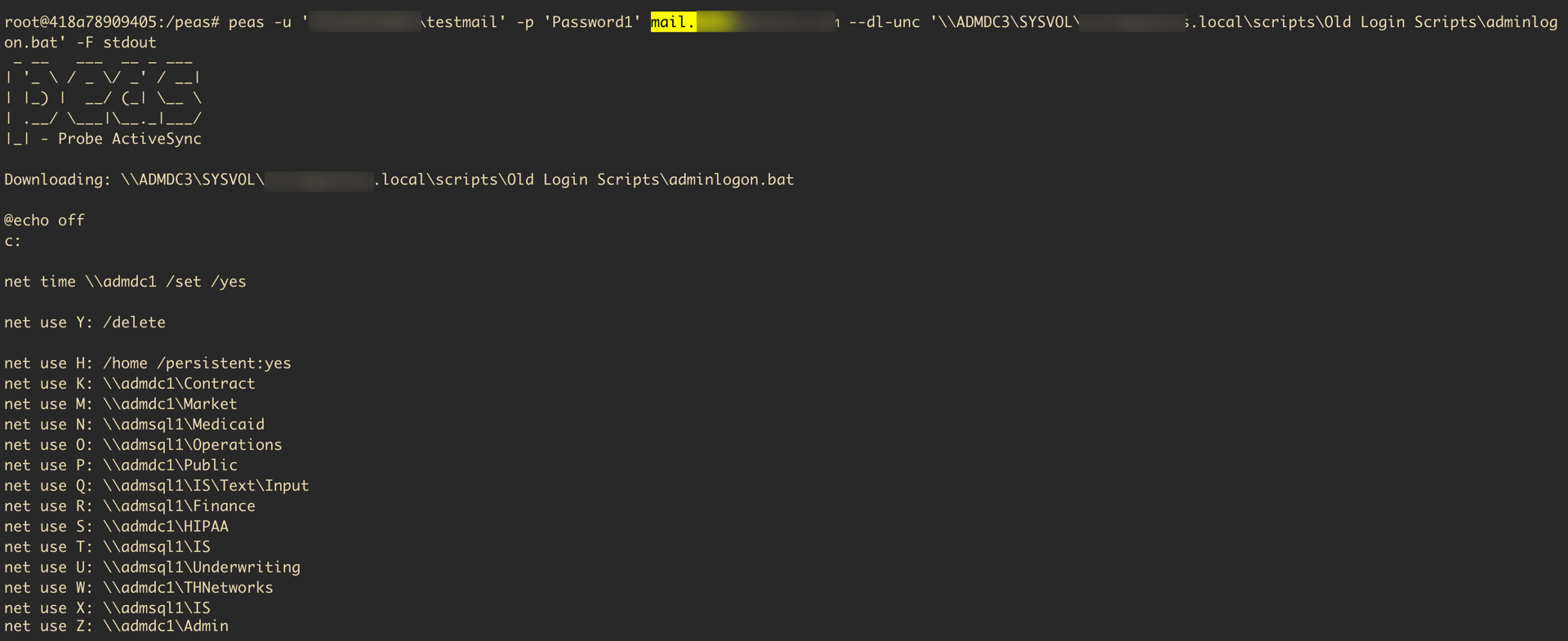
While searching for sensitive information, Sprocket came across a Microsoft Excel spreadsheet containing passwords for all service accounts and other sensitive information. Contained within this file was an account that did NOT require MFA to connect to the company VPN.
Sprocket logged in using this account and gained access to the internal network. Other credentials were then used from the same Excel spreadsheet to traverse the network as a domain administrator. Sprocket could then access all company PII and extract password hashes from the domain controller.
Path to remediation
First and foremost, always enforce a policy that does the following:
-
Asks users not to store passwords in cleartext
-
Encourage and train employees on how to use a password safe to securely store such sensitive information.
Most employee’s hate managing passwords. Password managers are not something they often dislike, but instead aren’t aware of. When an organization provides a great solution for them to manage their many passwords, they often flock to the opportunity.
In security-awareness trainings, encourage and educate employees on the use of secure password managers. This not only protects your employees’ credentials but also saves IT time and money.
This goes for IT staff as well; they’re often the biggest offenders. In the case study above, IT admins stored passwords in the offending Excel spreadsheet. If anyone needs to use a shared password manager, it’s IT. Don’t let staff fall short here, as it could lead to significant financial and reputational damage to your organization.
An additional step we can take to reduce the chances of this happening is to audit which network users are able to access certain file shares. We recommend that approach, because we won’t ever be able to properly audit and catch all instances of cleartext credentials storage. It’s a pipe dream in large companies with thousands of users.
More often than not, we find that once we have credentialed access to a network, we can access all files stored on shares without issue. This is bad! Instead, we want to make sure we restrict access to different file shares based on an employee’s role in the organization. A great high-level overview of this process is detailed in the article from Microsoft listed below:

Access Control Overview (Windows 10) - Microsoft 365 Security
When a new network share or folder is created, institute a change management process to specifically review and implement granular folder permissions for domain users. If anything, IT teams reading this article most likely know the highest risk shares on the network. Do the following to protect those shares:
-
Create a list of sensitive network shares.
-
Audit their usage by network users.
-
Collaborate and create a list of users or groups that should be able to access that network share.
-
Institute permission changes that restrict access to those users and groups.
-
Create a change request form that ensures any future users added to the network share are the ones who need it.
-
Periodically review network file share permissions. You can even do this with offensive tooling for a little more fun and a different perspective on your network.
A final step we can take is to implement monitoring that can detect an attacker’s attempt to search filesystems for words like:
-
password
-
credentials
-
id_rsa
In certain situations, attackers will gain access to a user’s workstation and then want to search accessible network shares for sensitive information. They’ll use commands like this:
findstr /spin "password" *.*
dir /s *pass* == *cred* == *vnc* == *.config*
This shouldn’t go unoticed on your network. Build detections to catch this command in action. No legitimate user would do this. At least with detections we can catch attackers in the act instead of finding out that’s how they deployed ransomware.
Wrap-up
Don’t let this be the thing that results in your company’s network being compromised. This just feels like a crazy issue to even be discussing in 2021, but it’s legitimate and one you need to take seriously.




