Introduction
This is start of a series I'm calling Autored. My goal is to quickly stand up temporary systems I commonly use during an engagement. Other efforts in this area have been documented, but they are more complex and time consuming to manage. I only use Terraform and bash scripts to keep customization easy and simple. In 3 minutes, you can have a fresh install of Empire with listeners and stagers ready to go.
Prerequisites
You'll need the following:
- Working install of Terraform
- Permissions and ssh keys to your cloud environment (I'll demo a setup in AWS)
- The autored github repo
Step 1 - Installing terraform
Download the proper Terraform package for you operating system.
Terraform is very simple to install because its just a single binary.
Extract the zip unzip terraform_0.11.1_linux_amd64.zip and copy it to your binary path cp terraform /usr/local/bin/terraform.
Thats it! Test that its working by just executing terraform
Step 2 - Setup users & permissions in the cloud
You will need two things for AWS.
- ssh keys for direct access
- IAM user with permissions (don't use your root account, you know better!)
Create a ssh key pair:
- In the AWS console, go to services (upper left)
- Select EC2 under the Compute section.
- Select Key Pairs in the nav on the left.
- Select Create Key Pair and name it 'redteam'.
- Download and save the key to ~/.ssh/redteam.pem
Create a new IAM user, set the needed permissions, and copy over your keys. It's quick:
- In the AWS console, go to services (upper left)
- Select IAM under the Security, Identity & Compliance section
- In IAM, select Users in the nav on the left.
- Select Add user
- Fill out a User name, and for access type, select programmatic access. Click Next.
- Select the tab/box that's labeled Attach existing policies directly. Add the following policy: AmazonEC2FullAccess. Click Next, than Create user
- Copy the access key and secret for the ~/.aws/credentials file (next step)
Create a file in ~/.aws/credentials with the following in it:
[autored]
aws_access_key_id = REPLACE_WITH_YOUR_OWN
aws_secret_access_key = REPLACE_WITH_YOUR_OWN
region = us-east-2Step 3 - Download and configure the Autored template
Clone the autored-empire repo:
git clone https://github.com/sprocketsecurity/autored-empireNote: I download and rename this repo each time for new clients to stay organized. Example:
git clone https://github.com/sprocketsecurity/autored-empire autored-empire-CLIENTNAME
There is a sub directory for each cloud provider. Right now I only support AWS. The config directory contains scripts and files that Terraform will upload and run on the instance during provisioning.
Initialize Terraform. cd into auto-empire/aws then run the following:
terraform initConfiguration
The configs assume a couple things:
- You have downloaded your ssh key pair and saved it to ~/.ssh/redteam.pem.
To change it: update the aws_priv_key variable in autored-empire/aws/variables.tf. - You'r AWS region is us-east-2
To change it: update the provider section in autored-empire/aws/main.tf.
Step 4 - Launch
You must be in the directory that contains main.tf to launch Terraform. In this case, auto-empire/aws:
terraform applyYou will see all the output, and in roughly 3 minutes you should have a working Empire instance. The script will output the public IP of the instance and the ssh command to access it.
Access
You can access Empire by sshing to the host and running: screen -x empire.
A http 80 and 443 listener is setup automatically. The setup script outputs Powershell stagers for both listeners.
They will saved to the ~/Empire directory and named stager-http80.txt and stager-http443.txt. Once Empire is ready, you should have an output similar to the screenshot below:
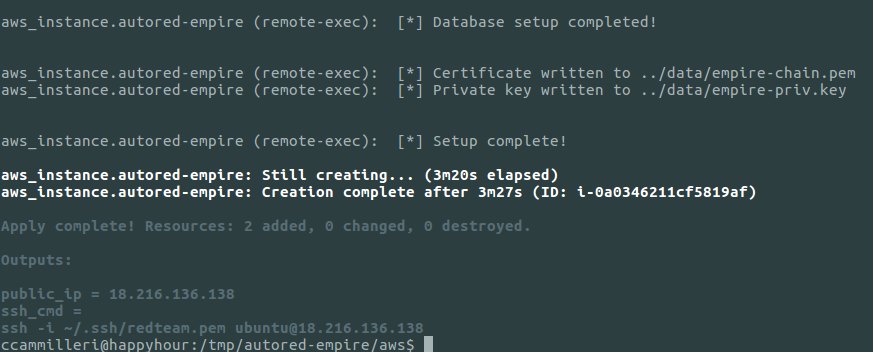
Terraform usage
Here are some helpful Terraform commands:
Destroy the host/plan:
terraform destroyCheck for syntax errors in your terraform scripts:
terraform validateCan't remember if the host is running? or do you want to get the public IP again from the output?
terraform showTips and Troubleshooting
- Most issues are related with IAM permissions and key pairs. Pay attention to the Terraform warnings, they usually point you in the right direction.
- Verify your profile name in ~/.aws/credentials is set to autored
- Verify your region is correct in the provider section of autored-empire/aws/main.tf
- Try not to delete instances and security groups via the AWS web console. Use
terraform destroyinstead. - variables.tf contains a client name variable that adds a tag of Client=YOUR_CLIENT_NAME to the instance.
- You can customize the Empire setup via the bash script located in autored-empire/configs/empire_setup.bash.




